Summary
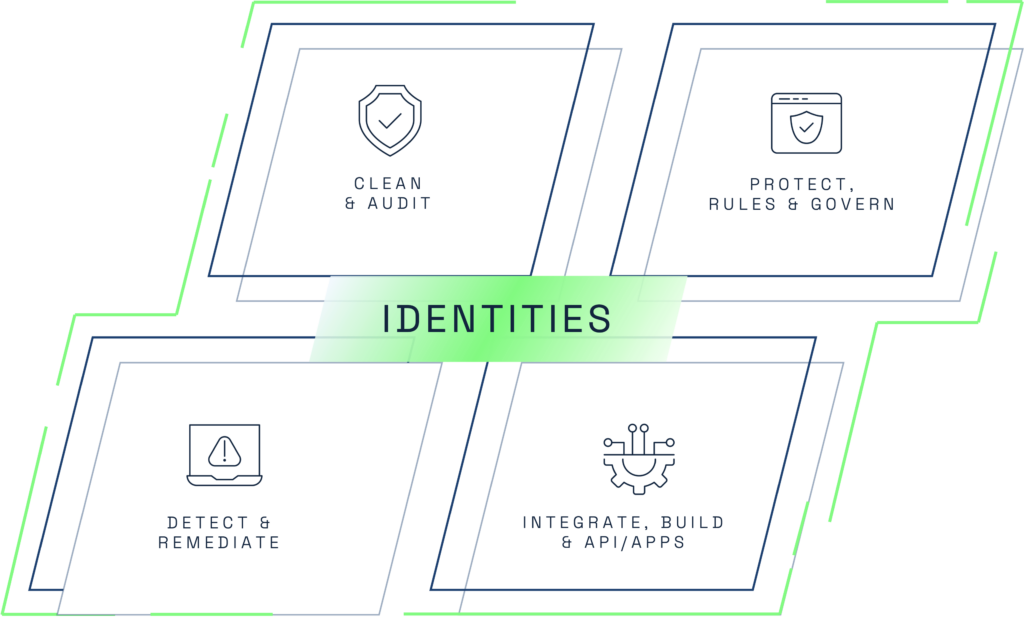
In today’s increasingly digital landscape, protecting identity stands as the single most critical mission for any Chief Information Security Officer (CISO). Cyber threats continue to evolve, targeting the very core of an organization’s security infrastructure—its identities. Effective identity protection is critical to safeguarding sensitive data and ensuring organizational resilience against cyber attacks. Here are the five steps every CISO must undertake to secure their organization’s identities:
1.) Clean and Audit Current Identities
Thorough cybersecurity audit services and cleanup of existing identities are essential. This includes:
- Active Directory (AD): Regularly reviewing and updating user accounts to remove any that are inactive or obsolete. Read our blog post on AD Best Practices here – /10-best-practices-for-active-directory-security
- Service Accounts: Ensuring that service accounts are properly managed, with appropriate lifecycle controls in place.
- Embedded Credentials: Identifying and securing hardcoded credentials within applications and scripts.
- Lowest Permissions: Implementing the principle of least privilege to ensure users and services have only the access necessary to perform their roles.
- Groups and Privileges: Regularly auditing group memberships and privileges to prevent privilege creep and unnecessary access.
2.) Implement a Robust Privileged Access Management (PAM) Solution
A robust PAM solution is critical in managing and securing privileged accounts. Key features should include:
- Password Rotation: Automated and frequent rotation of passwords for privileged accounts to reduce the risk of compromise.
- RDP to Servers: Secure Remote Desktop Protocol (RDP) access to servers to ensure that all sessions are authorized and monitored.
- SSO/MFA: Implementing Single Sign-On (SSO) and Multi-Factor Authentication (MFA) to enhance access security.
- Session Recording: Recording privileged sessions to provide an audit trail and facilitate forensic analysis in the event of a security incident.
3.) Integrate Critical Solutions to the PAM
To maximize the effectiveness of your PAM solution, it must be integrated with other critical security tools and systems within your organization. This integration allows for seamless communication and data sharing, enhancing the overall security posture. Key integrations include:
- SIEM (Security Information and Event Management) Systems: For real-time monitoring and analysis of security events.
- ITSM (IT Service Management) Tools: To ensure that all privileged access is properly managed and documented through change management processes.
- Identity Governance and Administration (IGA) Solutions: To maintain continuous oversight of user identities and access rights.
4.) Secure Applications and Application Development
Securing applications and their development processes is vital to protecting identities. This includes:
- Application Security: Implementing security measures within the application lifecycle to protect against vulnerabilities and exploits.
- API Security: Ensuring that APIs are secured to prevent unauthorized access and data breaches.
- Secure Development Practices: Adopting secure coding practices and conducting regular code reviews and security testing.
5.) Implement a Generative-AI Solution within Your Cybersecurity Stack
Generative AI can significantly enhance your cybersecurity efforts by:
- Threat Detection: Leveraging AI to detect and respond to threats in real time.
- Identity Analytics: Using AI to analyze user behavior and identify anomalies that may indicate compromised identities.
- Active Remediation: Implementing AI-driven automation to quickly and efficiently remediate security incidents. This involves active remediation using alerting systems, a Security Operations Center (SOC), and cybersecurity engineers working within a Cyber Incident Response Team (CIRT). These components work together to ensure immediate response to threats, minimizing damage and recovery time.
By adopting these five critical steps, CISOs can exponentially reduce the threats to their organizations. While protection and detection are crucial, it is best to assume the root cause of cybersecurity incidents lies in identities.
Partnering with Cyberhill Partners for Comprehensive Identity Protection
At Cyberhill Partners, we specialize in providing comprehensive identity protection solutions tailored to your organization’s unique needs. With over 800 complex cybersecurity implementations completed, our team has the expertise to help you:
- Conduct thorough identity audits and cleanups.
- Implement and manage robust PAM solutions.
- Integrate critical security tools to enhance your PAM.
- Secure your applications and development processes.
- Leverage advanced AI solutions within your cybersecurity stack.
With Cyberhill Partners, you can be assured of a proactive and strategic approach to identity protection, significantly reducing your organization’s exposure to cyber threats. Protect your identities, protect your business. Contact us today to learn more about our services and how we can help you achieve unparalleled security.

Cyberhill’s Wolverine: The M&A Solution

Forbes Feature: The Untapped Power Of Unstructured Data In Enterprise AI
